Google\’s cybersecurity team has recently issued a warning regarding a new cyber threat. In this particular attack, malicious individuals are taking advantage of the Google Calendar service to carry out command-and-control operations. This technique, known as Google Calendar RAT (GCR), transforms a user\’s calendar into a channel for cyber-attacks. The threat actors behind this method have even shared a public proof-of-concept (PoC) on underground forums to spread awareness of their approach.

During their routine threat analysis, Google discovered a vulnerability that had been present on GitHub since June 2023 and was being discussed on criminal forums, as outlined in their Eighth Threat Horizons report. Although there have been no reported instances of GCR being actively exploited, the potential threat is being treated with utmost seriousness.
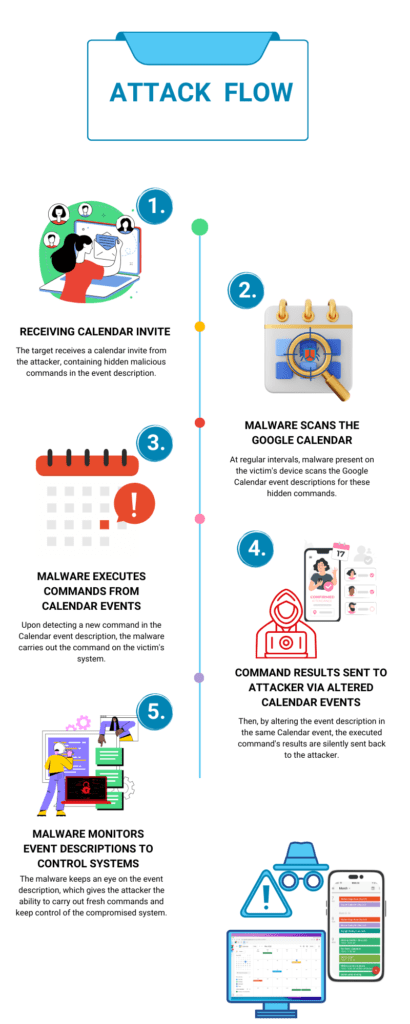
Attack Workflow
- The target receives a calendar invite from the attacker, containing hidden malicious commands in the event description.
- At regular intervals, malware present on the victim\’s device scans the Google Calendar event descriptions for these hidden commands.
- Upon detecting a new command in the Calendar event description, the malware carries out the command on the victim\’s system.
- Then, by altering the event description in the same Calendar event, the executed command\’s results are silently sent back to the attacker.
- The malware keeps an eye on the event description, which gives the attacker the ability to carry out fresh commands and keep control of the compromised system.
Defenders face a challenging responsibility of detecting and preventing malicious activities, while also ensuring that legitimate operations are not disrupted, due to the exploitation of trust in Google\’s services.
Mitigation Measures
To ensure the security of Google Calendar usage, various mitigation measures can be considered:
- Monitor Event Invitation: Examining every calendar invitation with great attention, especially those that come from unknown sources.
- Behavior Analysis: Implementing tools to examine user behavior and identify irregularities in Google Calendar use.
- Strict Permissions: Organizations should set strict permission guidelines for calendar events.
- Regular security audits: Regular audits look for unusual connections or applications with access rights to user and calendar information.
- User education: Teach users how to spot suspicious activity and warn them about the risks of receiving unfamiliar calendar invites.
- Endpoint Security: Making use of endpoint security programs to identify and stop suspicious activity patterns that might indicate to a C2 channel.
After the detection of this threat, Gmail accounts associated with the identified malicious activities have been disabled by Google, strengthening its defenses against comparable threats. It is strongly advised for both individual users and businesses to adopt these suggested measures in order to improve their security posture and safeguard the integrity of their systems from such concealed cyber-attack strategies.
Empower Your Defense with AYRIME’s Security services!
At AYRIME, we are not only committed to keeping you informed about the latest security news, but we also provide you with a robust shield against the evolving threat landscape. With our team of expert advisors by your side, we ensure that your digital realm remains resilient in the face of the most current security challenges.
Don’t just stay informed, stay resilient!
Reach out to us today to elevate your security posture and embark on a proactive journey of protection!


