Discover the best security testing tool for your needs with our comprehensive comparison of SAST, DAST, and IAST methods.

As the digital transformation wave sweeps across industries, the importance of developing secure, high-performing software has never been more crucial. Applications are the engines driving businesses forward, and any glitch, whether functional or security-related, can halt progress or even reverse it. This is where comprehensive application security testing steps in, ensuring that software is not just efficient but also fortified against potential threats.
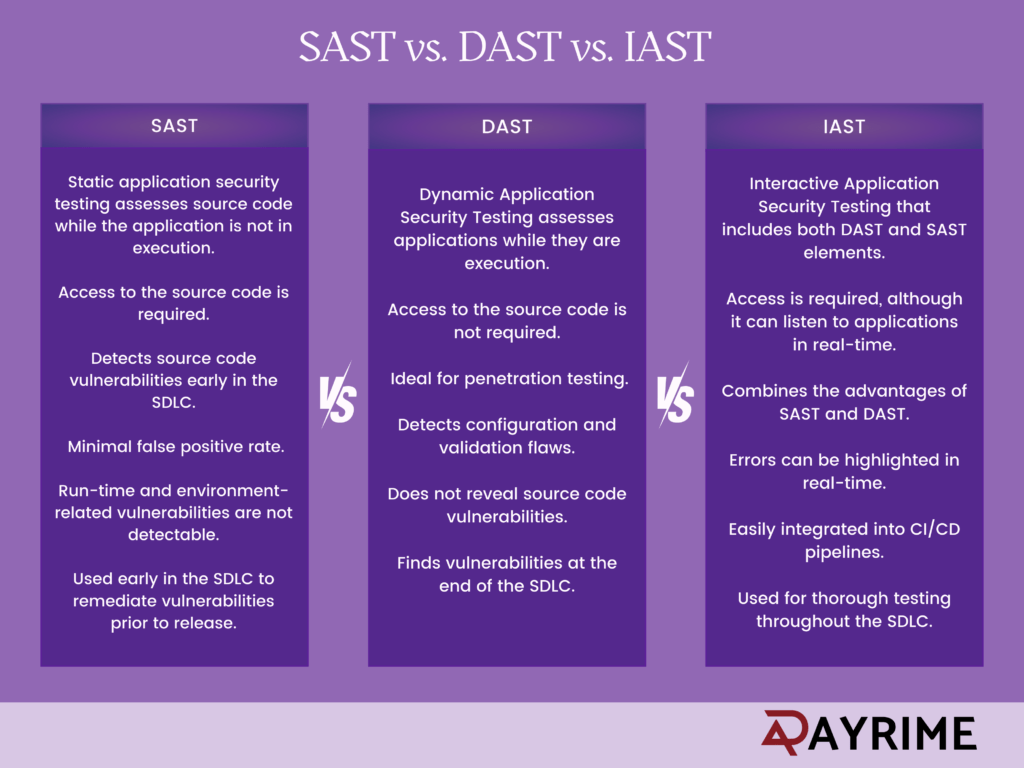
Static Application Security Testing (SAST)
What is SAST?
Static Application Security Testing (SAST) is a white-box testing technique that focuses on inspecting application source code, bytecode, or binary code without executing it. SAST ensures more secure software by identifying potential vulnerabilities by analyzing the inner workings of the code.
When to use SAST?
SAST should be incorporated early in the Software Development Life Cycle (SDLC). It works best in the early stages of development, when developers may find and fix vulnerabilities prior to the final release of the application.
Pros and Cons of SAST
Pros:
- Early Detection: Identifies vulnerabilities in their early phases.
- Comprehensive: Examines every line of code.
- Speed: Rapidly reviews large volumes of code.
Cons:
- False Alerts: May produce inaccurate findings.
- Code Access: Requires the source code to be evaluated.
Dynamic Application Security Testing (DAST)
What is DAST?
DAST, also referred to as black box testing, is a security testing technique that actively monitors running programs to find any potential vulnerabilities. Instead of evaluating code, DAST examines the exposed interfaces and behaviors of a running application for vulnerabilities. By providing businesses with real-time insights into how web applications operate during production, DAST technologies enable them to proactively resolve any vulnerabilities and stop hackers from exploiting them.
When to use DAST?
DAST should be utilized both after development and during runtime, particularly when assessing web applications that could be vulnerable to external threats. Since many attacks, such as cross-site scripting and SQL injections, take advantage of vulnerabilities that arise while an application is operating, DAST offers protection by identifying potential security breaches before they are exploited.
Pros and Cons of DAST
Pros:
- Independence: Operates independently of the application.
- Real-Time Detection: Finds vulnerabilities that can be exploited in real-time.
- No Need for Source Code: It is not necessary to have access to an application\’s source code.
Cons:
- Inexact location: Does not identify the exact code place where a vulnerability is present.
- Expertise Required: To analyze the results, security knowledge is necessary.
- Time-intensive: Tests may take a long time.
Interactive Application Security Testing (IAST)
What is IAST?
IAST (Interactive Application Security Testing) is an innovative testing approach that integrates attributes of both static (SAST) and dynamic (DAST) testing methods. IAST focuses on analyzing code in real time when the program is operating. Through the deployment of agents or sensors within the program, it records vulnerability and behavior in real-time, providing developers with exact code modifications that improve security.
When to use IAST?
IAST is flexible and can be integrated at various stages of the Software Development Life Cycle (SDLC), from development to production. It is most effective when used in integration testing, as it can identify vulnerabilities that are spread among several components.
Pros and Cons of IAST
Pros:
- Real-time Feedback: Provides thorough, instantaneous coverage and insights. Comprehensive
- Analysis: Examines several aspects, including the code, environment variables, inputs, outputs, and runtime of the application.
Cons:
- Performance Impact: Can cause the application to run a little slower.
- Monitoring Required: Application monitoring is required for proper operation.
IAST emerges as an essential asset in our ever-changing digital environment. It not only gives developers accurate, fast feedback but also gives them the ability to properly strengthen apps, reducing potential threats. Businesses may proactively close security weaknesses and ensure reliable and secure software delivery by prioritizing IAST.
Conclusion
SAST, DAST, and IAST are essential tools in a developer\’s toolbox when it comes to software security. While DAST analyzes running applications to find vulnerabilities in real-time activities, SAST provides early detection by assessing code without execution. IAST offers thorough insights into an application\’s security posture during runtime by integrating the advantages of both approaches. The suitable approach is determined by the specific requirements of a project, its stage in the SDLC, and the desired depth of analysis. Businesses may strengthen their defense against potential cyber threats by recognizing and leveraging the particular benefits of each strategy.

